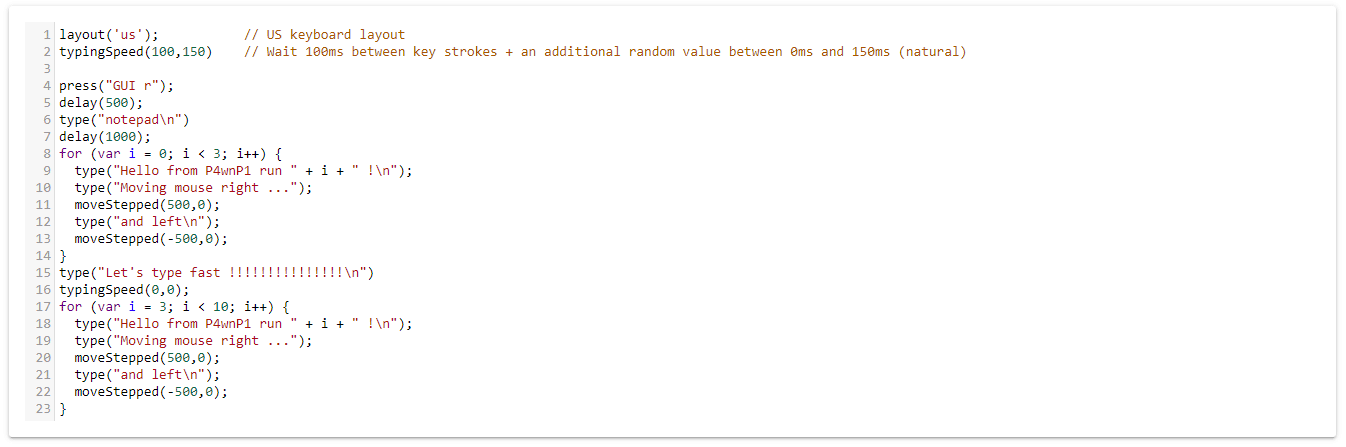
P4wnP1-ALOA is a very handy tool that I always keep in my hacking bag. You could compare it to a Rubber Ducky, it can simulate a USB mouse, keyboard, and USB flash drive to carry out sophisticated attacks. It comes preloaded with a handy web interface to manage itself and runs on top of Kali Linux. It has been some time since it has seen an update but I have never had a single issue with it even in its current state. I have only tested this using the Raspberry Pi 0 W v1.1 I can not guarantee it will work on any other versions.
What can I do with it?
Ever seen in a movie or show when a hacker plugs what looks like a flash drive into someone’s computer and it steals data or installs a virus? Anything you can do via keyboard or mouse we are going to be able to do. Things like executing PowerShell scripts, downloading stagers, or even just stealing WiFi credentials.
Downloading P4wnP1-ALOA
You can grab your own image on the releases page on GitHub. At the time of writing the file name is “kali-linux-v0.1.1-beta-rpi0w-nexmon-p4wnp1-aloa.img.xz”. After extracting, write the image to your SD card and insert it into your Raspberry Pi 0 W. Plug in the power cord, it will be plugged into the furthest port from the HDMI for power, and the other port for running attacks. Wait about 2 minutes for it to power on the first time and continue.
Logging in for the first time
You should see a new wireless network appear with a strange-looking name “💥🖥💥 Ⓟ➃ⓌⓃ🅟❶”, the default password is “MaMe82-P4wnP1” without quotes. After connecting open your browser and go to:
http://172.24.0.1:8000You will see the web interface with some options we need to configure.

Change the above options to something less suspicious, you could use something like Manufacture Name: Dell or HP, Product Name Dell USB Keyboard. Try to think of something that would not look suspicious. Once you have these values set we can move on to the next section.

By default Mass Storage is disabled, you will probably want this enabled unless you plan on using some other method of exfiltrating data if you do enable it you need to disable CDC ECM. When using Mass Storage you can store files directly on the Raspberry Pi after grabbing them. Another method you can use is email but some corporate networks block unknown email servers.
Unless you want to have to re-do your settings were going to want to save and deploy them. To save our settings click the “Store” button, and a dialogue box will appear type in “startup”, and click “store”. Click the blue deploy button and look for any errors at the top of the screen.
Head on over to the WiFi Settings tab
If I saw the wireless network pop up with a device exploding and the word p4wn I would be a little suspicious. Let’s make this something more discreet.

The two settings were going to want to change here, are SSID and pre-shared key. You can also choose to select “Hide SSID” if you want to be even a little more discreet. After changing the settings we’re going to click “Store”, enter the name “startup” and click “store”. You will get disconnected when you click deploy so you will need to re-connect to your newly named network.
Work Complete
Give yourself a pat on the back, if you made it here you are ready to go! You can now start writing your HID Script.